
标题: 孔明传伤害显示补丁代码 [打印本页]
作者:
ctermiii 时间: 2010-8-1 14:28 标题: 孔明传伤害显示补丁代码
对于孔明传的伤害已经分析的差不多了,因此想着出个伤害显示补丁;
由于原来的伤害计算函数里,蛇兵和象兵在计算的时候会直接写入混乱状态,致命一击也会显示,
这对模拟伤害很不利,只好重新写了一下。蛇兵和象兵实际伤害可能也会变化0~5点;
但我军正常似乎也没有这两个兵种的,所以不影响。
使用方法:
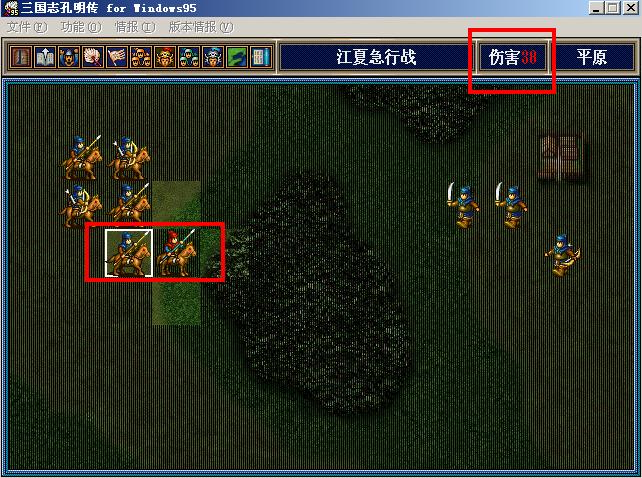
打上补丁后,选择攻击、策略、道具,游戏画出攻击范围亮区后,
鼠标移动到敌人身上,会在本该显示敌人名字的地方,
就是图中右上角的方框地方,显示的就是本次攻击预计伤害;
伤害以敌人当前耐久力为上限,超过的话将显示敌人当前耐久力;
因为必须以实际攻击时候的相对地形计算,所以攻击范围以外的对敌武将伤害仅供参考,条件相同的情况下结果是一样的。
其他情况下正常显示。
8.2更新:
1、更新内容:第1条代码内容,其他未动,第一次攻击之后不升级的情况下能判断是否连击;
2、累计两次伤害,最大上限仍旧不能超过武将当前耐久力;
3、连击粉红色显示;
见图
具体情况看图以及附件
相关代码:
1、多写的代码,来计算策略以及物理伤害:
004813A0 . 00000000 DD 00000000 ;一个全局变量开关
004813A4 C9 DB C9 ;
004813A5 CB DB CB
004813A6 BA DB BA
004813A7 A6 DB A6
004813A8 1B DB 1B
004813A9 . 43 32 25 75 0>ASCII "C2%u",0
004813AE 00 DB 00
004813AF 00 DB 00
格式化字符串:伤害�C2%u...
其中的32为字符颜色控制码红色,更换则可变为其他颜色
004813B0 /$ 53 PUSH EBX
004813B1 |. 57 PUSH EDI
004813B2 |. 56 PUSH ESI
004813B3 |. 8B75 08 MOV ESI,DWORD PTR SS:[EBP+8]
004813B6 |. 55 PUSH EBP
004813B7 |. 8BEC MOV EBP,ESP
004813B9 |. 83EC 20 SUB ESP,20
004813BC |. 33C0 XOR EAX,EAX
004813BE |. 33DB XOR EBX,EBX
004813C0 |. 8A1D A1134800 MOV BL,BYTE PTR DS:[4813A1]
004813C6 |. A0 A3134800 MOV AL,BYTE PTR DS:[4813A3]
004813CB |. 6BC0 17 IMUL EAX,EAX,17
004813CE |. 05 98C04600 ADD EAX,edk2kmz.0046C098
004813D3 |. 8945 E0 MOV DWORD PTR SS:[EBP-20],EAX
004813D6 |. 8B00 MOV EAX,DWORD PTR DS:[EAX]
004813D8 |. 6BC0 36 IMUL EAX,EAX,36
004813DB |. 05 E8564500 ADD EAX,edk2kmz.004556E8
004813E0 |. 8945 E8 MOV DWORD PTR SS:[EBP-18],EAX
004813E3 |. 8BC6 MOV EAX,ESI
004813E5 |. 6BC0 17 IMUL EAX,EAX,17
004813E8 |. 05 98C04600 ADD EAX,edk2kmz.0046C098
004813ED |. 8945 E4 MOV DWORD PTR SS:[EBP-1C],EAX
004813F0 |. 8B00 MOV EAX,DWORD PTR DS:[EAX]
004813F2 |. 6BC0 36 IMUL EAX,EAX,36
004813F5 |. 05 E8564500 ADD EAX,edk2kmz.004556E8
004813FA |. 8945 EC MOV DWORD PTR SS:[EBP-14],EAX
004813FD |. 895D F0 MOV DWORD PTR SS:[EBP-10],EBX
00481400 |. 33C0 XOR EAX,EAX
00481402 |. 8945 F4 MOV DWORD PTR SS:[EBP-C],EAX
00481405 |> 8945 F8 /MOV DWORD PTR SS:[EBP-8],EAX
00481408 |. A0 A0134800 |MOV AL,BYTE PTR DS:[4813A0]
0048140D |. 8BF0 |MOV ESI,EAX
0048140F |. 4E |DEC ESI
00481410 |. 74 1F |JE SHORT edk2kmz.00481431
00481412 |. 8B45 F0 |MOV EAX,DWORD PTR SS:[EBP-10]
00481415 |. 0FB6B8 B0D244>|MOVZX EDI,BYTE PTR DS:[EAX+44D2B0]
0048141C |. 33C9 |XOR ECX,ECX
0048141E |. B1 06 |MOV CL,6
00481420 |. 33D2 |XOR EDX,EDX
00481422 |. F7F1 |DIV ECX
00481424 |. C1E0 04 |SHL EAX,4
00481427 |. 09F8 |OR EAX,EDI
00481429 |. 8945 F0 |MOV DWORD PTR SS:[EBP-10],EAX
0048142C |. 4E |DEC ESI
0048142D |. 74 46 |JE SHORT edk2kmz.00481475
0048142F |. EB 5C |JMP SHORT edk2kmz.0048148D
00481431 |> 6A 01 |PUSH 1
00481433 |. 8B45 EC |MOV EAX,DWORD PTR SS:[EBP-14]
00481436 |. 50 |PUSH EAX
00481437 |. 8B4D E0 |MOV ECX,DWORD PTR SS:[EBP-20]
0048143A |. E8 6E90FAFF |CALL edk2kmz.0042A4AD
0048143F |. 8945 FC |MOV DWORD PTR SS:[EBP-4],EAX
00481442 |. 85C0 |TEST EAX,EAX
00481444 |. 7E 2A |JLE SHORT edk2kmz.00481470
00481446 |. 8B4D E0 |MOV ECX,DWORD PTR SS:[EBP-20]
00481449 |. E8 488FFAFF |CALL edk2kmz.0042A396
0048144E |. 0FB6D8 |MOVZX EBX,AL
00481451 |. 6A 64 |PUSH 64 ; /Arg1 = 00000064
00481453 |. E8 D05EFCFF |CALL edk2kmz.00447328 ; \edk2kmz.00447328
00481458 |. 83C4 04 |ADD ESP,4
0048145B |. 3BD8 |CMP EBX,EAX
0048145D |. 7E 11 |JLE SHORT edk2kmz.00481470
0048145F |. 8B45 FC |MOV EAX,DWORD PTR SS:[EBP-4]
00481462 |. 8D0440 |LEA EAX,DWORD PTR DS:[EAX+EAX*2]
00481465 |. 99 |CDQ
00481466 |. 2BC2 |SUB EAX,EDX
00481468 |. D1E8 |SHR EAX,1
0048146A |. 8945 FC |MOV DWORD PTR SS:[EBP-4],EAX
0048146D |. FF45 F8 |INC DWORD PTR SS:[EBP-8]
00481470 |> E9 2B000000 |JMP edk2kmz.004814A0
00481475 |> 8B45 F0 |MOV EAX,DWORD PTR SS:[EBP-10]
00481478 |. 50 |PUSH EAX ; /Arg2
00481479 |. 8B45 EC |MOV EAX,DWORD PTR SS:[EBP-14] ; |
0048147C |. 50 |PUSH EAX ; |Arg1
0048147D |. 8B4D E0 |MOV ECX,DWORD PTR SS:[EBP-20] ; |
00481480 |. E8 5C73F8FF |CALL edk2kmz.004087E1 ; \edk2kmz.004087E1
00481485 |. 8945 FC |MOV DWORD PTR SS:[EBP-4],EAX
00481488 |. E9 13000000 |JMP edk2kmz.004814A0
0048148D |> 8B45 F0 |MOV EAX,DWORD PTR SS:[EBP-10]
00481490 |. 50 |PUSH EAX ; /Arg2
00481491 |. 8B45 EC |MOV EAX,DWORD PTR SS:[EBP-14] ; |
00481494 |. 50 |PUSH EAX ; |Arg1
00481495 |. 8B4D E0 |MOV ECX,DWORD PTR SS:[EBP-20] ; |
00481498 |. E8 6A74F8FF |CALL edk2kmz.00408907 ; \edk2kmz.00408907
0048149D |. 8945 FC |MOV DWORD PTR SS:[EBP-4],EAX
004814A0 |> 837D FC 00 |CMP DWORD PTR SS:[EBP-4],0
004814A4 |. 0F8E 81000000 |JLE edk2kmz.0048152B
004814AA |. 8B4D EC |MOV ECX,DWORD PTR SS:[EBP-14]
004814AD |. E8 CE7DF8FF |CALL edk2kmz.00409280
004814B2 |. 0FB6C0 |MOVZX EAX,AL
004814B5 |. 50 |PUSH EAX ; /Arg1
004814B6 |. E8 6D5EFCFF |CALL edk2kmz.00447328 ; \edk2kmz.00447328
004814BB |. 83C4 04 |ADD ESP,4
004814BE |. 8BD8 |MOV EBX,EAX
004814C0 |. 8B4D E8 |MOV ECX,DWORD PTR SS:[EBP-18]
004814C3 |. E8 B87DF8FF |CALL edk2kmz.00409280
004814C8 |. 0FB6C0 |MOVZX EAX,AL
004814CB |. 50 |PUSH EAX ; /Arg1
004814CC |. E8 575EFCFF |CALL edk2kmz.00447328 ; \edk2kmz.00447328
004814D1 |. 83C4 04 |ADD ESP,4
004814D4 |. 3BD8 |CMP EBX,EAX
004814D6 |. 72 06 |JB SHORT edk2kmz.004814DE
004814D8 |. 837D F8 01 |CMP DWORD PTR SS:[EBP-8],1
004814DC |. 75 21 |JNZ SHORT edk2kmz.004814FF
004814DE |> 8B4D E8 |MOV ECX,DWORD PTR SS:[EBP-18]
004814E1 |. E8 9A7DF8FF |CALL edk2kmz.00409280
004814E6 |. 0FB6C0 |MOVZX EAX,AL
004814E9 |. 50 |PUSH EAX ; /Arg1
004814EA |. E8 395EFCFF |CALL edk2kmz.00447328 ; \edk2kmz.00447328
004814EF |. 83C4 04 |ADD ESP,4
004814F2 |. 33C9 |XOR ECX,ECX
004814F4 |. 33D2 |XOR EDX,EDX
004814F6 |. B1 06 |MOV CL,6
004814F8 |. F7F1 |DIV ECX
004814FA |. 0155 FC |ADD DWORD PTR SS:[EBP-4],EDX
004814FD |. EB 2C |JMP SHORT edk2kmz.0048152B
004814FF |> 8B4D EC |MOV ECX,DWORD PTR SS:[EBP-14]
00481502 |. E8 797DF8FF |CALL edk2kmz.00409280
00481507 |. 0FB6C0 |MOVZX EAX,AL
0048150A |. 50 |PUSH EAX ; /Arg1
0048150B |. E8 185EFCFF |CALL edk2kmz.00447328 ; \edk2kmz.00447328
00481510 |. 83C4 04 |ADD ESP,4
00481513 |. 33C9 |XOR ECX,ECX
00481515 |. 33D2 |XOR EDX,EDX
00481517 |. B1 06 |MOV CL,6
00481519 |. F7F1 |DIV ECX
0048151B |. 52 |PUSH EDX ; /Arg2
0048151C |. 8B45 FC |MOV EAX,DWORD PTR SS:[EBP-4] ; |
0048151F |. 50 |PUSH EAX ; |Arg1
00481520 |. E8 A65DFCFF |CALL edk2kmz.004472CB ; \edk2kmz.004472CB
00481525 |. 83C4 08 |ADD ESP,8
00481528 |. 8945 FC |MOV DWORD PTR SS:[EBP-4],EAX
0048152B |> A0 A0134800 |MOV AL,BYTE PTR DS:[4813A0]
00481530 |. 3C 01 |CMP AL,1
00481532 |. 75 62 |JNZ SHORT edk2kmz.00481596
00481534 |. A1 18184500 |MOV EAX,DWORD PTR DS:[451818]
00481539 |. 85C0 |TEST EAX,EAX
0048153B |. 75 50 |JNZ SHORT edk2kmz.0048158D
0048153D |. 8B4D E0 |MOV ECX,DWORD PTR SS:[EBP-20]
00481540 |. E8 518EFAFF |CALL edk2kmz.0042A396
00481545 |. 0FB6D8 |MOVZX EBX,AL
00481548 |. 8B4D E4 |MOV ECX,DWORD PTR SS:[EBP-1C]
0048154B |. E8 468EFAFF |CALL edk2kmz.0042A396
00481550 |. 0FB6C0 |MOVZX EAX,AL
00481553 |. 3BD8 |CMP EBX,EAX
00481555 |. 7C 3F |JL SHORT edk2kmz.00481596
00481557 |. 2BD8 |SUB EBX,EAX
00481559 |. 43 |INC EBX
0048155A |. 6A 0F |PUSH 0F ; /Arg1 = 0000000F
0048155C |. E8 C75DFCFF |CALL edk2kmz.00447328 ; \edk2kmz.00447328
00481561 |. 83C4 04 |ADD ESP,4
00481564 |. 3BD8 |CMP EBX,EAX
00481566 |. 7E 2E |JLE SHORT edk2kmz.00481596
00481568 |. 8B4D E4 |MOV ECX,DWORD PTR SS:[EBP-1C]
0048156B |. 8B49 0F |MOV ECX,DWORD PTR DS:[ECX+F]
0048156E |. 8B45 FC |MOV EAX,DWORD PTR SS:[EBP-4]
00481571 |. 3BC1 |CMP EAX,ECX
00481573 |. 73 21 |JNB SHORT edk2kmz.00481596
00481575 |. 8945 F4 |MOV DWORD PTR SS:[EBP-C],EAX
00481578 |. 33C0 |XOR EAX,EAX
0048157A |. 40 |INC EAX
0048157B |. A3 18184500 |MOV DWORD PTR DS:[451818],EAX
00481580 |. C605 AA134800>|MOV BYTE PTR DS:[4813AA],33 ;连击颜色
00481587 |. 48 |DEC EAX
00481588 |.^ E9 78FEFFFF \JMP edk2kmz.00481405
0048158D |> 33C0 XOR EAX,EAX
0048158F |. A3 18184500 MOV DWORD PTR DS:[451818],EAX
00481594 |. EB 07 JMP SHORT edk2kmz.0048159D
00481596 |> C605 AA134800>MOV BYTE PTR DS:[4813AA],32 ;正常颜色
0048159D |> 8B45 FC MOV EAX,DWORD PTR SS:[EBP-4]
004815A0 |. 0345 F4 ADD EAX,DWORD PTR SS:[EBP-C]
004815A3 |. 8B4D E4 MOV ECX,DWORD PTR SS:[EBP-1C]
004815A6 |. 8B49 0F MOV ECX,DWORD PTR DS:[ECX+F]
004815A9 |. 3BC1 CMP EAX,ECX
004815AB |. 7E 02 JLE SHORT edk2kmz.004815AF
004815AD |. 8BC1 MOV EAX,ECX
004815AF |> 83C4 20 ADD ESP,20
004815B2 |. 5D POP EBP
004815B3 |. 5E POP ESI
004815B4 |. 5F POP EDI
004815B5 |. 5B POP EBX
004815B6 \. C3 RETN
2、策略攻击地方显示激活:
00404444 |. /74 27 JE SHORT edk2win.0040446D
00404446 |. |0FB645 F8 MOVZX EAX,BYTE PTR SS:[EBP-8]
0040444A |. |8B0485 B0D144>MOV EAX,DWORD PTR DS:[EAX*4+44D1B0]
00404451 |. |50 PUSH EAX
00404452 |. |0FB645 F4 MOVZX EAX,BYTE PTR SS:[EBP-C]
00404456 |. |8B0485 A8D144>MOV EAX,DWORD PTR DS:[EAX*4+44D1A8]
0040445D |. |50 PUSH EAX
0040445E |. |68 F8DE4400 PUSH edk2win.0044DEF8
00404463 |. |6A 00 PUSH 0
00404465 |. |E8 CB4A0300 CALL edk2win.00438F35
0040446A |. |83C4 10 ADD ESP,10
0040446D |> \6A 00 PUSH 0 ; /Arg1 = 00000000
0040446F |. B9 00FB4600 MOV ECX,edk2win.0046FB00 ; |
00404474 |. E8 C7510000 CALL edk2win.00409640 ; \edk2win.00409640
00404479 |. 0FB645 F8 MOVZX EAX,BYTE PTR SS:[EBP-8]
0040447D |. 85C0 TEST EAX,EAX
0040447F |. 74 0C JE SHORT edk2win.0040448D
00404481 |. 6A 01 PUSH 1 ; /Arg1 = 00000001
00404483 |. B9 00FB4600 MOV ECX,edk2win.0046FB00 ; |
00404488 |. E8 B3510000 CALL edk2win.00409640 ; \edk2win.00409640
0040448D |> 8A45 0C MOV AL,BYTE PTR SS:[EBP+C] ;策略显示开关ON
00404490 |. 0FC8 BSWAP EAX
00404492 |. 8A65 08 MOV AH,BYTE PTR SS:[EBP+8]
00404495 |. 8A45 10 MOV AL,BYTE PTR SS:[EBP+10]
00404498 |. 0905 A0134800 OR DWORD PTR DS:[4813A0],EAX
0040449E |. 33C0 XOR EAX,EAX
004044A0 |. 50 PUSH EAX ; /Arg3 => 00000000
004044A1 |. 8A45 FC MOV AL,BYTE PTR SS:[EBP-4] ; |
004044A4 |. 0C 80 OR AL,80 ; |
004044A6 |. 50 PUSH EAX ; |Arg2
004044A7 |. 8B45 0C MOV EAX,DWORD PTR SS:[EBP+C] ; |
004044AA |. 50 PUSH EAX ; |Arg1
004044AB |. B9 00FB4600 MOV ECX,edk2win.0046FB00 ; |
004044B0 |. E8 008A0300 CALL edk2win.0043CEB5 ; \edk2win.0043CEB5
004044B5 |. 8845 F0 MOV BYTE PTR SS:[EBP-10],AL
004044B8 |. 33C0 XOR EAX,EAX
004044BA |. 2105 A0134800 AND DWORD PTR DS:[4813A0],EAX ;策略显示开关OFF
004044C0 |. 8A45 F0 MOV AL,BYTE PTR SS:[EBP-10]
004044C3 |. 3D FF000000 CMP EAX,0FF
004044C8 |. 0F84 73020000 JE edk2win.00404741
004044CE |. 8B45 F0 MOV EAX,DWORD PTR SS:[EBP-10]
004044D1 |. 50 PUSH EAX
004044D2 |. 8B45 0C MOV EAX,DWORD PTR SS:[EBP+C]
004044D5 |. 50 PUSH EAX
004044D6 |. E8 C8090000 CALL edk2win.00404EA3
004044DB |. 83C4 08 ADD ESP,8
004044DE |. 0FB645 F0 MOVZX EAX,BYTE PTR SS:[EBP-10]
004044E2 |. 6BC0 17 IMUL EAX,EAX,17
004044E5 |. 8D88 98C04600 LEA ECX,DWORD PTR DS:[EAX+46C098]
3、物理攻击地方显示激活:
0041D99E |. E8 9DBCFEFF CALL edk2win.00409640 ; \edk2win.00409640
0041D9A3 |. E9 52000000 JMP edk2win.0041D9FA
0041D9A8 |> 33C0 XOR EAX,EAX
0041D9AA |. 8A45 FC MOV AL,BYTE PTR SS:[EBP-4]
0041D9AD |. 83F8 0E CMP EAX,0E
0041D9B0 |. 0F85 11000000 JNZ edk2win.0041D9C7
0041D9B6 |. 6A 02 PUSH 2 ; /Arg1 = 00000002
0041D9B8 |. B9 00FB4600 MOV ECX,edk2win.0046FB00 ; |
0041D9BD |. E8 7EBCFEFF CALL edk2win.00409640 ; \edk2win.00409640
0041D9C2 |. E9 33000000 JMP edk2win.0041D9FA
0041D9C7 |> 33C0 XOR EAX,EAX
0041D9C9 |. 8A45 FC MOV AL,BYTE PTR SS:[EBP-4]
0041D9CC |. 83F8 19 CMP EAX,19
0041D9CF |. 0F85 11000000 JNZ edk2win.0041D9E6
0041D9D5 |. 6A 03 PUSH 3 ; /Arg1 = 00000003
0041D9D7 |. B9 00FB4600 MOV ECX,edk2win.0046FB00 ; |
0041D9DC |. E8 5FBCFEFF CALL edk2win.00409640 ; \edk2win.00409640
0041D9E1 |. E9 14000000 JMP edk2win.0041D9FA
0041D9E6 |> 0FB645 FC MOVZX EAX,BYTE PTR SS:[EBP-4]
0041D9EA |. 3C 1A CMP AL,1A
0041D9EC |. 75 0C JNZ SHORT edk2win.0041D9FA
0041D9EE |. 6A 04 PUSH 4 ; /Arg1 = 00000004
0041D9F0 |. B9 00FB4600 MOV ECX,edk2win.0046FB00 ; |
0041D9F5 |. E8 46BCFEFF CALL edk2win.00409640 ; \edk2win.00409640
0041D9FA |> 6A 00 PUSH 0
0041D9FC |. 8B4D F4 MOV ECX,DWORD PTR SS:[EBP-C]
0041D9FF |. E8 6AC90000 CALL edk2win.0042A36E
0041DA04 |. 50 PUSH EAX ; |Arg2
0041DA05 |. 8B45 F4 MOV EAX,DWORD PTR SS:[EBP-C] ; |
0041DA08 |. 8A40 04 MOV AL,BYTE PTR DS:[EAX+4] ; |物理攻击显示开关ON
0041DA0B |. 50 PUSH EAX ; |Arg1
0041DA0C |. 83E0 3F AND EAX,3F ; |
0041DA0F |. C1E0 18 SHL EAX,18 ; |
0041DA12 |. 40 INC EAX ; |
0041DA13 |. 0905 A0134800 OR DWORD PTR DS:[4813A0],EAX ; |
0041DA19 |. 90 NOP ; |
0041DA1A |. B9 00FB4600 MOV ECX,edk2win.0046FB00 ; |
0041DA1F |. E8 91F40100 CALL edk2win.0043CEB5 ; \edk2win.0043CEB5
0041DA24 |. 8845 F8 MOV BYTE PTR SS:[EBP-8],AL
0041DA27 |. 33C0 XOR EAX,EAX
0041DA29 |. 2105 A0134800 AND DWORD PTR DS:[4813A0],EAX ;物理攻击显示开关OFF
0041DA2F |. 8A45 F8 MOV AL,BYTE PTR SS:[EBP-8]
0041DA32 |. 90 NOP
0041DA33 |. 3C FF CMP AL,0FF
0041DA35 |. 74 52 JE SHORT edk2win.0041DA89
0041DA37 |. 8B45 F8 MOV EAX,DWORD PTR SS:[EBP-8]
0041DA3A |. 50 PUSH EAX
0041DA3B |. 8B45 F4 MOV EAX,DWORD PTR SS:[EBP-C]
0041DA3E |. 8A40 04 MOV AL,BYTE PTR DS:[EAX+4]
0041DA41 |. 50 PUSH EAX
0041DA42 |. E8 96B8FFFF CALL edk2win.004192DD
0041DA47 |. 83C4 08 ADD ESP,8
0041DA4A |. 6A 00 PUSH 0
0041DA4C |. 6A 01 PUSH 1
0041DA4E |. 0FB645 F8 MOVZX EAX,BYTE PTR SS:[EBP-8]
0041DA52 |. 6BC0 17 IMUL EAX,EAX,17
0041DA55 |. 8D88 98C04600 LEA ECX,DWORD PTR DS:[EAX+46C098]
0041DA5B |. E8 70080000 CALL edk2win.0041E2D0
4、名字显示激活与替换:
0043AE5E /$ 55 PUSH EBP
0043AE5F |. 8BEC MOV EBP,ESP
0043AE61 |. 83EC 08 SUB ESP,8
0043AE64 |. 53 PUSH EBX
0043AE65 |. 56 PUSH ESI
0043AE66 |. 57 PUSH EDI
0043AE67 |. 894D F8 MOV DWORD PTR SS:[EBP-8],ECX
0043AE6A |. 0FB645 08 MOVZX EAX,BYTE PTR SS:[EBP+8]
0043AE6E |. 3C FF CMP AL,0FF
0043AE70 |. 0F84 AE000000 JE edk2win.0043AF24
0043AE76 |. 3C 2D CMP AL,2D
0043AE78 |. 0F8D A6000000 JGE edk2win.0043AF24
0043AE7E |. 6BC0 17 IMUL EAX,EAX,17
0043AE81 |. 8D88 98C04600 LEA ECX,DWORD PTR DS:[EAX+46C098]
0043AE87 |. E8 FA2FFFFF CALL edk2win.0042DE86
0043AE8C |. 85C0 TEST EAX,EAX
0043AE8E |. 0F84 90000000 JE edk2win.0043AF24
0043AE94 |. 0FB645 08 MOVZX EAX,BYTE PTR SS:[EBP+8]
0043AE98 |. 6BC0 17 IMUL EAX,EAX,17
0043AE9B |. 8D88 98C04600 LEA ECX,DWORD PTR DS:[EAX+46C098]
0043AEA1 |. E8 DAE6FCFF CALL edk2win.00409580
0043AEA6 |. 8945 FC MOV DWORD PTR SS:[EBP-4],EAX
0043AEA9 |. E8 7C68FCFF CALL edk2win.0040172A
0043AEAE |. 6A 0C PUSH 0C
0043AEB0 |. BB 06000000 MOV EBX,6
0043AEB5 |. 8B45 FC MOV EAX,DWORD PTR SS:[EBP-4]
0043AEB8 |. 50 PUSH EAX ; /Arg1
0043AEB9 |. E8 ECC40000 CALL edk2win.004473AA ; \edk2win.004473AA
0043AEBE |. 83C4 04 ADD ESP,4
0043AEC1 |. 2BD8 SUB EBX,EAX ; |
0043AEC3 |. C1EB 01 SHR EBX,1 ; |
0043AEC6 |. 83C3 3D ADD EBX,3D ; |
0043AEC9 |. 53 PUSH EBX ; |Arg1
0043AECA |. B9 10BC4600 MOV ECX,edk2win.0046BC10 ; |
0043AECF |. E8 334DFEFF CALL edk2win.0041FC07 ; \edk2win.0041FC07
0043AED4 |. 837D 08 0F CMP DWORD PTR SS:[EBP+8],0F ;我方不替换
0043AED8 |. 7C 34 JL SHORT edk2win.0043AF0E
0043AEDA |. F705 A0134800>TEST DWORD PTR DS:[4813A0],3
0043AEE4 |. 74 28 JE SHORT edk2win.0043AF0E
0043AEE6 |. 6A 0C PUSH 0C ; /Arg2 = 0000000C
0043AEE8 |. 6A 3D PUSH 3D ; |Arg1 = 0000003D
0043AEEA |. B9 10BC4600 MOV ECX,edk2win.0046BC10 ; |
0043AEEF |. E8 134DFEFF CALL edk2win.0041FC07 ; \edk2win.0041FC07
0043AEF4 |. A1 203B4500 MOV EAX,DWORD PTR DS:[453B20] ;系统随机数保存
0043AEF9 |. 50 PUSH EAX ; /Arg1 => 00000001
0043AEFA |. E8 B1640400 CALL edk2win.004813B0 ; 伤害计算
0043AEFF |. 59 POP ECX ;系统随机数恢复
0043AF00 |. 890D 203B4500 MOV DWORD PTR DS:[453B20],ECX
0043AF06 |. 50 PUSH EAX
0043AF07 |. 68 A4134800 PUSH edk2win.004813A4 ;伤害显示
0043AF0C |. EB 09 JMP SHORT edk2win.0043AF17
0043AF0E |> 8B45 FC MOV EAX,DWORD PTR SS:[EBP-4]
0043AF11 |. 50 PUSH EAX
0043AF12 |. 68 EC334500 PUSH edk2win.004533EC
0043AF17 |> 68 10BC4600 PUSH edk2win.0046BC10
0043AF1C |. E8 025CFEFF CALL edk2win.00420B23
0043AF21 |. 83C4 0C ADD ESP,0C
0043AF24 |> 5F POP EDI
0043AF25 |. 5E POP ESI
0043AF26 |. 5B POP EBX
0043AF27 |. C9 LEAVE
0043AF28 \. C2 0400 RETN 4
[ 本帖最后由 ctermiii 于 2010-8-2 11:37 编辑 ]
 图片附件:
shanghai.JPG (2010-8-1 14:29, 89.2 K) / 该附件被下载次数 346
图片附件:
shanghai.JPG (2010-8-1 14:29, 89.2 K) / 该附件被下载次数 346
http://xycq.org.cn/forum/attachment.php?aid=100183
 附件:
edk2kmz.rar (2010-8-2 11:36, 127.59 K) / 该附件被下载次数 526
附件:
edk2kmz.rar (2010-8-2 11:36, 127.59 K) / 该附件被下载次数 526
http://xycq.org.cn/forum/attachment.php?aid=100197
 图片附件:
2shanghai.JPG (2010-8-2 11:37, 85.92 K) / 该附件被下载次数 331
图片附件:
2shanghai.JPG (2010-8-2 11:37, 85.92 K) / 该附件被下载次数 331
http://xycq.org.cn/forum/attachment.php?aid=100199

作者:
ctermiii 时间: 2010-8-1 14:56
这样可以方便规划每一步的攻击动作。
作者:
ctermiii 时间: 2010-8-2 11:39
更新连击判断以及伤害累计情况
作者:
lewulezo 时间: 2010-8-2 16:08
好强的功能
我想把这补丁整合到我的修改器里,支持给自定义的exe文件打上这个补丁。
作者:
ctermiii 时间: 2010-8-2 16:43
可以啊
好像还不仅仅如此,敌人的反击,也差不多是一个类型。
如果要做的全一点,可以预计除了已经有的普攻、全力一击、连击外
还可以增加敌人反击、敌人反击全力一击、敌人是否反击连击;
这样可以把我方预计伤害敌人和预计受伤的情况都囊括了;
再加上攻击性策略和道具攻击预测、恢复性策略道具效果预测、异常状态攻击预测、
完了,这样孔明传就没玩头了。
[ 本帖最后由 ctermiii 于 2010-8-2 16:49 编辑 ]
作者:
阿尔法孝直 时间: 2010-8-2 16:45 标题: 回复 #5 ctermiii 的帖子
如果可以的话把霹雳车对敌方9个人的全部伤害都显示出来
作者:
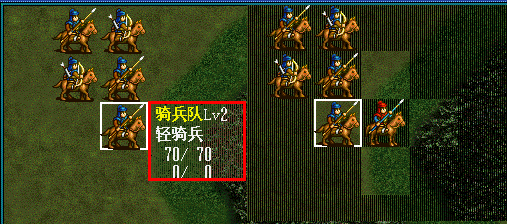
ctermiii 时间: 2010-8-2 16:57
游戏画出攻击范围后,点其他武将是没有该武将情报提示的;
如图方框
我原来打算把伤害显示在这里,后来发现还是1楼的更好看一点。
范围攻击的计算倒是不难,但显示有问题
估计要写的程序量太大了,而且没这么大地方显示。
 图片附件:
def.PNG (2010-8-2 16:57, 73.75 K) / 该附件被下载次数 334
图片附件:
def.PNG (2010-8-2 16:57, 73.75 K) / 该附件被下载次数 334
http://xycq.org.cn/forum/attachment.php?aid=100220
作者:
ctermiii 时间: 2010-8-2 16:59
其实有了单体伤害,其他都可以估算的,不考虑地形的话,差不多是单体的一半左右。
作者:
lewulezo 时间: 2010-8-2 17:13
好强的补丁。。
我打算把这个补丁弄到我的修改器里面,可以给自定义的exe文件打上这个补丁。
[ 本帖最后由 lewulezo 于 2010-8-2 17:25 编辑 ]
作者:
lewulezo 时间: 2010-8-2 17:21
打补丁时候发现,我和你的exe似乎不太一样,从0x1d9a3开始就不一样了。
下面是我的exe中的代码:
0001d9a3h: E9 58 00 00 00 33 C0 8A 45 FC 83 F8 0E 0F 85 11
0001d9b3h: 00 00 00 6A 02 B9 00 FB 46 00 E8 7E BC FE FF E9
0001d9c3h: 39 00 00 00 33 C0 8A 45 FC 83 F8 19 0F 85 11 00
0001d9d3h: 00 00 6A 03 B9 00 FB 46 00 E8 5F BC FE FF E9 1A
0001d9e3h: 00 00 00 33 C0 8A 45 FC 83 F8 1A 0F 85 0C 00 00
0001d9f3h: 00 6A 04 B9 00 FB 46 00 E8 40 BC FE FF 6A 00 8B
0001da03h: 4D F4 E8 64 C9 ...
不知道你的exe是从哪个版本开始修改的。
[ 本帖最后由 lewulezo 于 2010-8-2 17:24 编辑 ]
作者:
ctermiii 时间: 2010-8-2 18:04
压缩包的注释:
大小:187 MB (196,222,406 字节)
占用空间:187 MB (196,222,976 字节)
自己用一个什么工具脱的壳。
有几种可以脱壳的,脱出来一个大小:
536 KB (549,544 字节)
536 KB (548,864 字节)(我用的这个)
但这两个,在你说的位置,都一样
我知道了,我在本函数后边改写了代码,导致跳转位置变了,为了一致,我前边也改了,第一个改动位置就是你说的这个位置;
这个函数基本被重写了。
我第一帖蓝字里只是说明那一部分的作用,改动的地方远不止这么点。
第一帖除了1是自己写的,2、3、4都是压缩原来的代码来增加开关的,所以肯定有变化。。
[ 本帖最后由 ctermiii 于 2010-8-2 18:17 编辑 ]
作者:
阿尔法孝直 时间: 2010-8-17 02:03
有空的话把恢复类策略的恢复量也写上去
作者:
jasonfj 时间: 2011-2-11 16:36
好强的补丁,正在用,呵呵……
| 欢迎光临 轩辕春秋文化论坛 (http://xycq.org.cn/forum/) |
Powered by Discuz! 5.0.0 |







